Hi again,
This issue has came up too much, so I wanted to blog something short about this.
Prerequisites:
- Update (Added June 29th 2013) – If using Exchange 2013, check out Exchange 2013 Outlook Anywhere Considerations for some additional specific Exchange 2013 issues.
- Exchange 2007 or 2010
- Outlook 2003 / 2007 / 2010
- Windows XP / 7 / etc..
- Outlook Anywhere ( RPC over HTTP ) enabled – with Basic Authentication or NTLM Authentication
- Autodiscover – working correctly 😉
So, you’ve got it all configured, you enabled Outlook Anywhere, configured ISA 2006 / TMG / UAG to publish the Outlook Anywhere (or not), you published Autodiscover records an all is working great !
BUT ! you have this annoying user credentials pop ups, and users are going nuts ! and so do you !@ ( enough sarcasm ) it may work for a while, and then you are prompted again for user and password, or even worse – it might not work at all…
Here’s what can go wrong in bullets because we have a few different issues that might cause troubles..
- Outlook Anywhere is configured to use NTLM authentication:
- Solution 1 – Configure MSSTD or the Certificate Principle Name correctly (see below)
- Solution 2 – Configure your clients local security policy, in specific – LmCompatiblilityLevel to 2 or 3
- Solution 3 – If you try to pull NTLM with ISA / TMG / UAG, either configure “Kerberos Constrained Delegation” – check links below for the white-paper from Microsoft” or change the publishing rule to apply to “All Users” and in the Authentication Delegation tab choose the option “No delegation, but client may authenticate directly”
- SSL Certificates issues
- Outlook Anywhere was enabled for – mail.company.com (ExternalHostName), but you have a wildcard certificate or the certificate subject name does not match mail.company.com
- Solution – Configure MSSTD or the Certificate Principle Name correctly (see below)
- Outlook Anywhere continuously keep being configured automatically !%
So what’s that MSSTD or Certificate Principle Name ? well it’s a method Outlook can verify that the server you are connecting to indeed holds the correct SSL certificate subject name before sending credentials to.. well yeah it ain’t that secure.
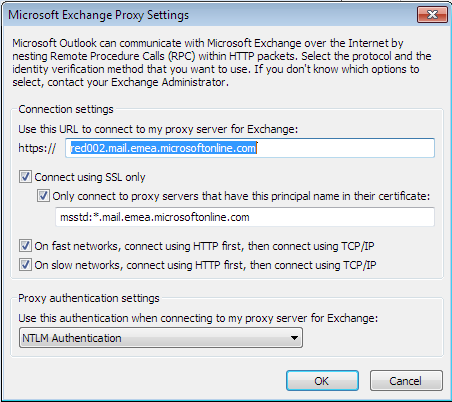
This setting is actually being configured automatically since Exchange 2007 and continue to be with Exchange 2010.
So here’s what you can do with it – all examples follow the Set Outlook Provider cmdlet syntax:CertPrincipalName
- You have a wildcard certificate – Run this command:
Set-OutlookProvider EXPR -CertPrincipalName msstd:*.company.com
- You have a differnet subject name on your SSL certificate then the ExternalHostName you configured for Outlook anywhere on your CAS server
Set-OutlookProvider EXPR -CertPrincipalName msstd:correctsubject.company.com
- You don’t want that “only connect to proxy servers that have this principle name in their certificate” check box marked at all ! 🙂
Set-OutlookProvider EXPR -CertPrincipalName none
New feature with Exchange 2010 – The Set-OutlookProvider cmdlet now allows Outlook 2010 clients to connect exclusively through RPC over HTTP (Outlook Anywhere) before trying RPC over TCP connections when connecting over the Internet. !
This means you can control the check box “On fast network, connect using HTTP first, then connect using TCP/IP”, here’s the two options:
- Always connect using HTTP (mark “on fast networks”) :
Set-OutlookProvider EXPR -OutlookProviderFlags:ServerExclusiveConnect
- User TCP/IP first then HTTP (default):
Set-OutlookProvider EXPR -OutlookProviderFlags:None
This should cover it, no more pop ups and hopefully Outlook Anywhere and you will be friends again !
ilantz
Credits (or links) :
When, if and how do you modify Outlook Providers?
Set-OutlookProvider
Publishing Outlook Anywhere Using NTLM Authentication With Forefront TMG or Forefront UAG
Exchange 2013 Outlook Anywhere Considerations
